Thousands of Americans affected by a healthcare cyberattack are now reviewing eligibility for $6000 dental data breach claims, part of a legal settlement tied to a ransomware intrusion at a U.S. dental provider in 2023. The case highlights growing risks to patient privacy as hackers increasingly target medical clinics, which store valuable identity and insurance data.
Table of Contents
$6000 Dental Data Breach Claims
| Key Fact | Detail / Statistic |
|---|---|
| Settlement value | About $1.2 million total |
| Potential compensation | Up to $6000 for documented losses |
| Affected patients | More than 200,000 individuals |
What the $6000 Dental Data Breach Claims Are About
A Wisconsin-based dental network, First Choice Dental Group, reported in late 2023 that unauthorized actors accessed its computer systems during a ransomware attack. According to court documents and settlement notices filed in U.S. federal court, attackers obtained sensitive patient information.
The compromised records included names, addresses, dates of birth, treatment information, and, in some cases, Social Security and insurance data. Legal filings state that affected individuals later filed a class-action lawsuit alleging the company failed to adequately protect patient data.
The dental provider denied wrongdoing but agreed to a financial settlement to resolve the claims and avoid prolonged litigation, a common outcome in U.S. privacy cases.
The lawsuit argued that patients faced ongoing risk because medical information cannot be replaced in the way credit cards can. While a bank can cancel a compromised card, a medical history or government identification number often remains permanently linked to a person.
Who Can Actually Receive Money
The widely shared figure — $6000 — does not apply to every patient. Instead, it represents reimbursement for documented losses.
Eligible compensation categories
- Identity-theft recovery expenses
- Fraudulent bank or credit charges
- Credit monitoring or legal fees
- Costs to replace identification documents
Patients without proof of financial harm may receive a smaller fixed payment and credit-monitoring services.
Legal experts say the structure is typical.
“Settlements like this are designed primarily to reimburse provable losses rather than distribute large universal payments,” said Ari Ezra Waldman, a privacy law professor at Northeastern University School of Law, in commentary frequently cited in data-privacy litigation analysis.
Attorneys involved in similar cases note that courts increasingly recognize the value of stolen personal data itself as a form of harm, even before financial loss occurs. However, compensation is still generally tied to measurable damages.
Why Healthcare Is a Prime Target for Hackers
(healthcare cybersecurity)
Healthcare organizations store a rare combination of personal and financial identifiers. A single patient record can contain enough information to open loans, file fraudulent insurance claims, or commit tax fraud.
The U.S. Department of Health and Human Services (HHS) has repeatedly warned that medical providers are increasingly targeted by ransomware groups. Federal breach reporting databases show that healthcare incidents regularly affect hundreds of thousands of people annually.
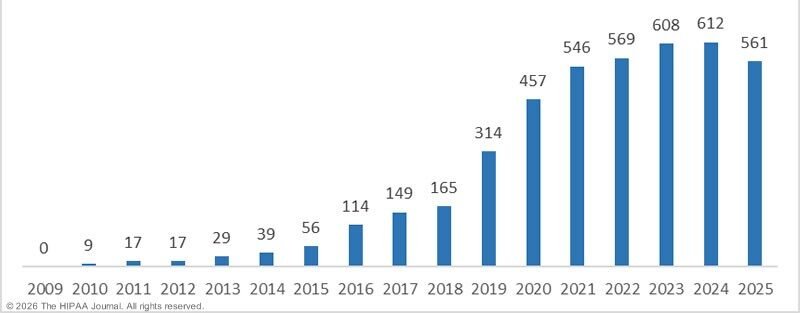
Cybersecurity researchers note that small clinics are especially vulnerable because they often lack dedicated security teams and rely on outdated software.
“Healthcare records are more valuable than credit card numbers because they cannot be easily changed,” said Brett Callow, a ransomware analyst at cybersecurity firm Emsisoft, in public briefings about medical sector attacks.
Why dental offices are especially vulnerable
Dental clinics frequently outsource IT systems, maintain digital X-rays, and connect multiple devices — scanners, imaging tools, and insurance software — to the same network. Each connection can create an entry point for attackers.
Many practices also operate as small businesses, making them less likely to employ full-time cybersecurity staff.
How Ransomware Attacks Work
(ransomware attack)
In a ransomware incident, criminals infiltrate a network, encrypt files, and demand payment for restoring access. However, modern attacks usually include a second step: data theft.
Hackers copy patient records and threaten to publish them online if the victim refuses to pay. Even when organizations restore systems, exposed information may still circulate on criminal marketplaces.
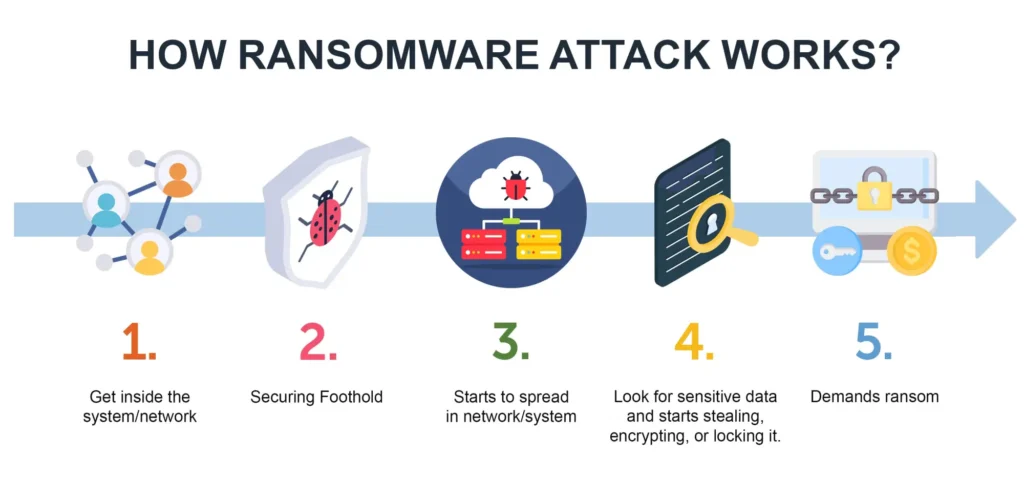
Common entry methods
Security investigators say most healthcare breaches begin with simple techniques:
- phishing emails sent to staff
- weak passwords
- outdated software patches
- remote desktop access left unsecured
Once inside, attackers often remain undetected for weeks.
What Criminals Do With Medical Data
Unlike stolen credit cards, healthcare records are rarely sold for quick purchases. Instead, criminals use them for long-term fraud schemes:
- filing fake insurance claims
- obtaining prescription drugs
- creating synthetic identities
- medical blackmail and extortion
Law enforcement agencies warn that medical identity theft can go unnoticed for years because victims rarely check insurance histories as frequently as bank accounts.
Broader Implications Beyond the United States
(identity theft protection)
Although the settlement applies only to specific U.S. patients, cybersecurity specialists say the lesson is global.
Dental clinics worldwide collect identification documents, phone numbers, insurance records, and payment details. In many countries, including India, those data points can enable SIM-swap fraud or unauthorized loans.
Consumer protection agencies often recommend the following after a breach:
- Monitor credit reports
- Enable two-factor authentication
- Freeze or lock biometric identity records where possible
- Report suspicious financial activity immediately
Historical Context: A Growing Pattern
The dental breach is part of a larger trend. Over the past decade, major hospital systems, laboratory chains, and insurance companies have all reported cyberattacks affecting millions of patients.
Healthcare cybersecurity analysts say attackers have shifted strategy. Previously, banks and retailers were primary targets. Financial institutions strengthened defenses, pushing criminals toward healthcare, where security spending historically lagged.
Cybersecurity think tanks report that ransomware groups increasingly operate as organized businesses, complete with customer support channels to negotiate payments.
Legal and Regulatory Context
The case reflects a broader legal trend. U.S. courts increasingly allow privacy lawsuits when companies fail to implement reasonable safeguards.
Healthcare providers are subject to the Health Insurance Portability and Accountability Act (HIPAA), which requires protection of medical information. Regulators can impose fines separate from civil lawsuits if violations are confirmed.
Some countries now require companies to notify affected patients within a specific number of days after discovering a breach. Regulators argue rapid notification allows people to secure bank accounts and identities before fraud occurs.
What Patients Should Check Now
Experts recommend reviewing any official notification letter received from a clinic or insurer. Real notices usually include:
- A description of the incident
- The date of exposure
- Contact information for identity-protection services
- Claim filing instructions
Cybersecurity authorities also warn that scammers frequently impersonate breach settlements to steal information. Patients should verify notices through the provider’s official website rather than links in unsolicited emails.
Immediate steps after a breach notice
- Change passwords on email and banking accounts
- Activate account alerts for transactions
- Review insurance claims history
- Save documentation for reimbursement claims
How to Tell a Real Settlement From a Scam
Authorities warn that large breach settlements often trigger secondary fraud. Criminals send fake compensation emails asking victims to “verify identity.”
Red flags include:
- urgent deadlines
- requests for OTP codes
- requests for full Social Security or bank login credentials
Real settlement administrators typically require only a claim form and documentation of expenses.
FAQs About $6000 Dental Data Breach Claims
Is everyone eligible for the $6000 payment?
No. Only affected patients who can document financial losses qualify for the highest reimbursement.
What if you never received a notification?
You are almost certainly not part of the settlement.
Why do companies settle even if they deny wrongdoing?
Settlements limit legal costs and uncertainty, which can exceed potential damages.
Can similar breaches happen elsewhere?
Yes. Healthcare providers globally face rising cyberattacks due to valuable patient data.
How long should you monitor your identity after a breach?
Cybersecurity experts recommend at least 12–24 months of monitoring because stolen data is often used months after the initial attack.